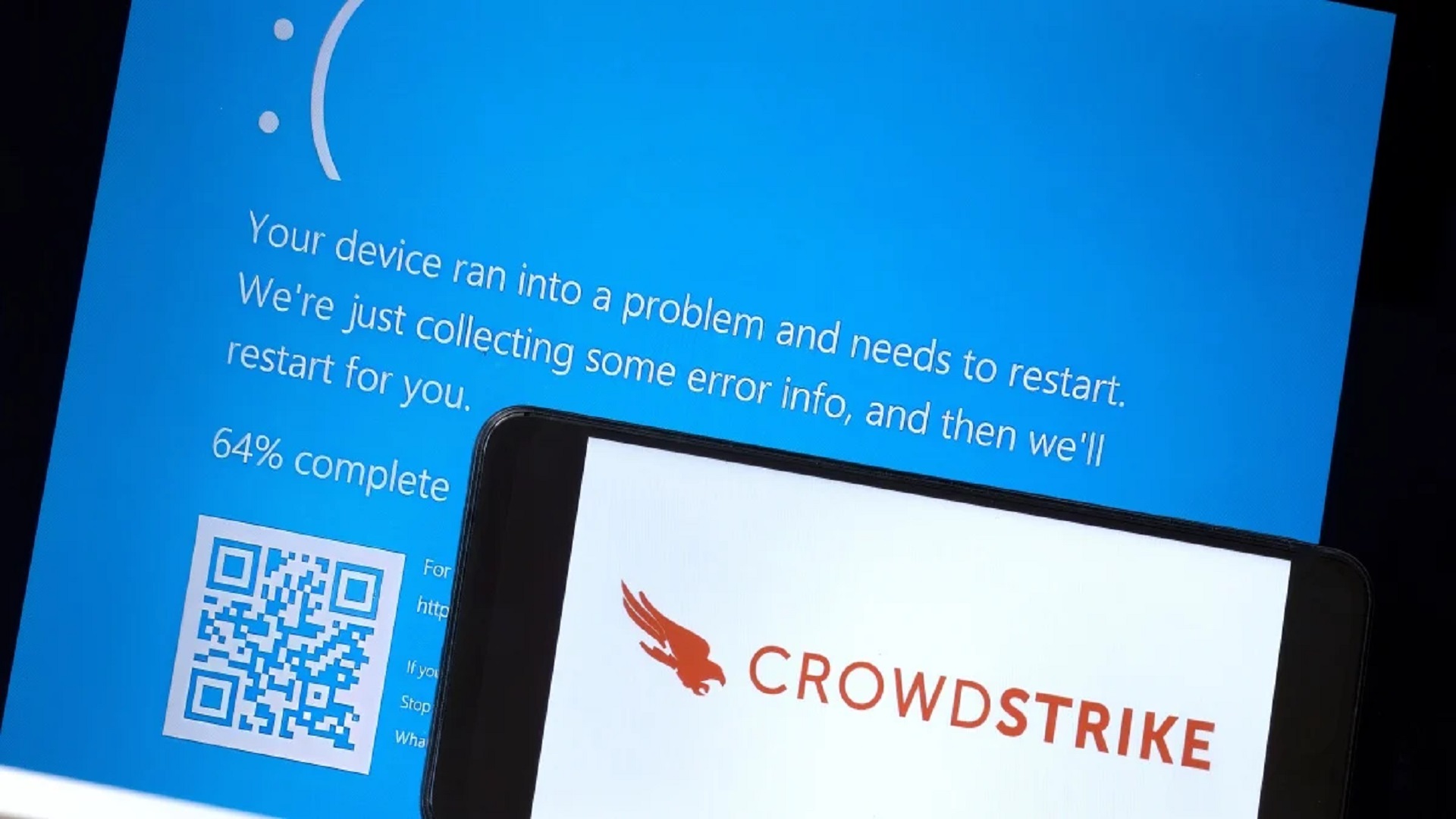
Earlier this month, a major disruption affected businesses worldwide due to a flawed security update provided by the US-based cybersecurity firm CrowdStrike for Microsoft Windows machines. This problematic update led to significant issues for airlines, banks, hospitals, and other essential services, impacting approximately 8.5 million Windows systems globally.
Both Microsoft and CrowdStrike have since released patches to address the issue, but restoring affected systems has taken several hours, and in some cases, even days. As is often the case during major tech outages, hackers and cybercriminals have seized the opportunity to exploit the situation. Cybersecurity agencies from various countries, including the US, UK, Australia, and Canada, have issued warnings about cyber attacks leveraging the CrowdStrike vulnerability.
In response, India’s cybersecurity agency CERT-In has also alerted local companies about potential threats related to the CrowdStrike outage. CERT-In’s advisory highlights ongoing phishing campaigns targeting CrowdStrike users. These campaigns include phishing emails masquerading as CrowdStrike support, impersonation of CrowdStrike staff via phone calls, and the sale of fraudulent recovery scripts and tools that may contain Trojan malware.
CERT-In cautioned that these attacks could deceive unsuspecting users into installing malicious software, potentially leading to data breaches, system crashes, and data loss.
To mitigate these threats, CERT-In has advised companies to block the following 25 URLs, which are considered dangerous:
crowdstrike.phpartners.Jorg
crowdstrike0day[.]com
crowdstrikebluescreen[-]com
crowdstrike-bsod[.]com
crowdstrikeupdate[.]com
crowdstrikebsod[..com
www.crowdstrike0day[.]com
www.fix-crowdstrike-bsod[.]com
crowdstrikeoutage[.]info
www.microsoftcrowdstrike[.]com
crowdstrikeoday[.]com
crowdstrike[.]buzz
www.crowdstriketoken[.]com
www.crowdstrikefix[..com
fix-crowdstrike-apocalypse[.]com
microsoftcrowdstrikel[.]com
crowdstrikedoomsday[.]com
crowdstrikedown[..com
whatiscrowdstrike[..com
crowdstrike-helpdesk[..com
crowdstrikefix[.]com
fix-crowdstrike-bsod[.]com
crowdstrikedown[.]site
crowdstuck[.]Jorg
Crowdfalcon-immed-update[.]com
crowdstriketoken[.]com
crowdstrikeclaim[.]com
crowdstrikeblueteam[.]com
crowdstrike-office365[.]com
crowdstrikefix[.]zip
crowdstrikereport[.]com