Blockchain technology, often dubbed as next major digital revolution after the advent of the internet, is essentially a general-purpose application of an existing technology, which is called “distributed ledger technology” (DLT). This technology essentially allows every person who is part of the blockchain network to verify the details of a transaction (for instance, how much money was paid to whom at what time) since a common “ledger” (which can be thought of a database) where all the transactions are recorded are “distributed” to every participant in the system, who individually verify the veracity of the transactions. This removes the need for an intermediary (such as a bank) having to act as central verifying authority.
Understanding the basics
A fundamental risk with our traditional, centralized systems is that they have a single (or a few) point of failure. Blockchain, being an application of DLT, solves this problem by making it harder for bad actors to leverage the system to the detriment of its users. Therefore, to understand blockchain, it is important to first understand what does DLT essentially mean. DLT is essentially used to maintain a decentralized database (i.e., the ledger), where the ledger is distributed across several users of the technology. Generally, in a DLT based service, every user of the service (called a ‘node’) maintains the ledger. Therefore, if any data changes happen, the ledger is updated by all nodes synchronically and continuously, therefore making the process decentralized by not requiring any single authority or system to record these changes. These nodes can use various mechanisms to verify and reach a common conclusion regarding the veracity of transactions on the ledger. The process by which nodes can arrive at this “consensus” is called the “consensus mechanism”. Reaching a consensus in a distributed system is very important as nodes must “agree” which transactions to add to the ledger, and which ones to reject.
How are transactions secure in this distributed system?
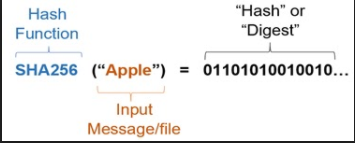
Transactions in a DLT-based system are secured using something called a Cryptographic Hash Function. A cryptographic hash function is an algorithm that takes an arbitrary amount of data (the input) – like a message or a transaction, for instance – and produces a fixed-size encrypted output of called a hash value: “hash.” A cryptographic hash function always gives the same output for a given input, but if you even slightly alter the input (the message), the corresponding hash changes completely. A cryptographic hash function encrypts the message in a secure manner so that it becomes infeasible to compute the contents of the message in reverse direction. This essentially means that one cannot guess the input (for example a word like “Apple”) from its encrypted message digest (which can be a string of seemingly random ones and zeros) without expending significant amounts of computing power that would in most cases render the enterprise of trying to decrypt the message futile. The cryptographic hash function is used in conjunction with other technologies like digital signatures, etc. that allow users on a network to easily verify if a transaction is correct or not, but not alter it.
A fundamental problem with distributed systems
Distributed systems face a fundamental problem in reaching consensus in a in a hierarchy-free network since a computer system or node may fail, and there is imperfect information across the other nodes regarding if and when a failure has occurred at a node. Computer systems must ensure that such faults do not stop the entire system from functioning. This problem is commonly known as the “Byzantine Fault” or the Byzantine generals’ problem.
The mitigation strategy employed by a system to ensure that such faults do not lead to complete system failure, is called Byzantine Fault Tolerance (BFT). A system is said to develop BFT when it can continue operating even if some of the nodes fail or act maliciously. That is to say, the nodes follow a method of arriving at a consensus on which transactions and in which order, to commit to the ledger in a distributed ledger system despite some nodes in the system malfunctioning. The mechanism through which these nodes reach this important consensus is called a Consensus Mechanism or a Consensus Protocol. There are various methods that DLT-based systems may employ to ensure BFT, such as Proof of Work, practical Byzantine Fault Tolerance, etc.
Enter: Blockchain
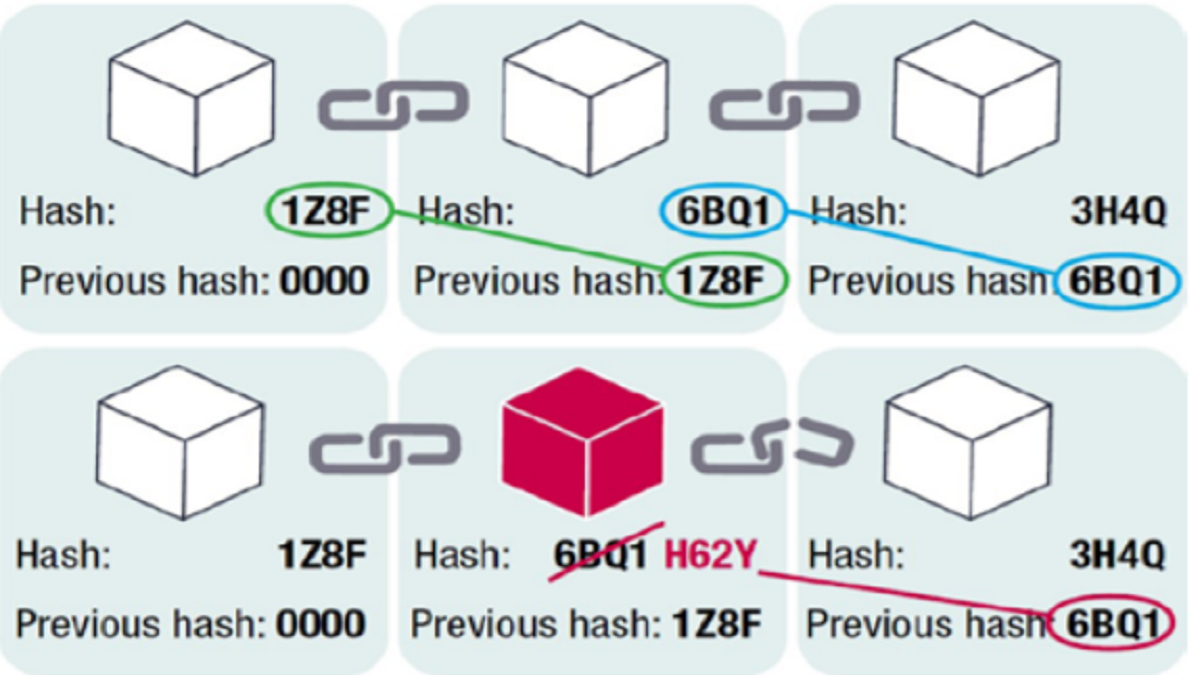
Fundamentally, blockchain is a combination of already existing technologies that together can create networks that secure trust between people or parties who otherwise have no reason to trust one another. Specifically, it utilizes DLT to store information verified by cryptography among a group of users, which is agreed through a pre-defined consensus mechanism. Each ‘block’ in a blockchain is akin to a page in the ledger, which contains the messages/transactions. Apart from the message/transaction data, the block is also secured by a hash, which acts as a unique fingerprint for the block, and the hash function for the block preceding it.
Tampering any data in a block (for instance, to alter any recorded transaction fraudulently), completely changes the hash of that block, thereby not allowing the next block to recognize the tampered block as part of the chain. This altered block would therefore not be recognized in the blockchain, allowing anyone to identify the exact transaction that was sought to be altered and maintaining the integrity of the chain.
While Cryptocurrency such as Bitcoin, Ethereum and many more are the most common and public facing applications of blockchain technology, different types of blockchains are being developed to suit different needs. Two of the most important features distinguishing the various types of blockchain are the “openness” of the platform (public or private) and the level of permissions required to add information to the blockchain (permissioned or permissionless).
Blockchain: Bringing Efficiency and Innovation
Blockchain technology has a potential to bring a lot of benefits in the market at a large scale in several sectors. For instance, some companies are experimenting with implementation of blockchain in supply chains. If effectively implemented, blockchain can bring in automated and better integrated inventory management. Supply chain blockchains, in particular, will be in demand due to ‘increased cost savings, enhanced traceability and greater transparency’. As per some reports, putting all of Asia Pacific’s trade-related paperwork into electronic form could slash the time it takes to export goods by up to 44 percent and cut costs by up to 31 percent. Companies are trying to scale and apply the technology to increase traceability of products in a supply chain, and decrease the time taken from days to seconds. If successful, tracing potentially hazardous food substances to a particular source such as a particular city or farm within a short time period would be a reality, allowing authorities to take effective steps and stay ahead of the curve in terms of managing cases where a disease may be highly communicable. Imagine the intended and effective application of this technology during our current crisis. Even as countries around the world are in a race to develop a vaccine or cure for COVID-19, ensuring smooth and efficient delivery of the vaccine to the most needed parts in the world is an entirely different challenge. A successfully deployed blockchain technology which streamlines supply chains in vaccine production and delivery across the globe can bring unprecedented value.
Some of these benefits can also be shared with competition authorities to regulate merger controls, cartel investigations and monitoring of abuse of dominance. For example, if all the evidence regarding company that is relevant for merger can be traced in a blockchain, it will be easier for authorities to assess correct economic evidences. This will increase transparency and reduce chances of getting misinformed by the parties. Similarly, in cartel investigations it may assist in case of leniency applications, where the applicant can provide all the economic evidences and history of transactions effectively to the authorities.
Understanding the Market
There can be several issues pertaining to horizontal agreements and vertical agreements. However, before delving deep into these issues, it is pertinent to assess how the market could be determined in future. There are several questions which may need to be answered by competition authorities. Would blockchain technology-based services compete with other existing technologies or would they come under a separate market for purposes of analysis of Competition Act (Act)? Will each blockchain be considered separate in its own and dominant in themselves? Further, considering that blockchains are meant for specific purposes, the market should depend on the type of blockchain and type of applications run of that blockchain. For example, blockchain for bitcoin will be completely different from a blockchain engaged in providing streamlined services for pharmaceutical companies.
Anticompetitive Agreements: Possible Concerns
Horizontal Agreements – There are three categories of players involved in a blockchain. These are developers, users and miners. In this case, collusion will mostly depend on the mechanism that a blockchain will follow. There can be collusion amongst all the miners, developers or users depending upon whether the blockchain is permissioned or permissionless. For example, in a private blockchain if the consensus mechanism is present in a manner that it provides maximum control to group of developers, there could be a case of collusion among the developers.
Controlling the consensus mechanism
Since a blockchain works on consensus mechanism, issue of collusion remains the prime concern. Especially in a private blockchain, since the protocols and consensus mechanism can be made in a way that essentially, control would rest with a limited number of people and not to the public. Using the same, such group of participants can alter the protocols of the blockchain without notifying other members, and eventually engage in practice of alteration of any transactions or information stored in any block. Once there is required consent in the chain, there can be a case of cartelization in such blockchain. Similarly, as discussed above, the same can be case in public blockchain if there is enough consent. For example, even though it may be difficult, but if one manages to establish coordination among majority of the mining pool owners, there is a possibility of collusion in bitcoin also.
Exchange of sensitive information
Exchange of sensitive business information is another aspect which may be achieved through blockchain. Such exchanges through blockchains can be used to collude and engage in anti competitive practices. Since the information is publicly available in a blockchain, it will be easier for enterprises to share information through which all the enterprises may collude easily. Considering the information on a blockchain can be updated on a real time basis, it can be used by colluding firms for their own advantages.
Additionally, because of anonymity that blockchain offers, it may be difficult for competition authorities to identify offenders and regulate conduct.
Enforcement of Cartel
Cartels usually enforce their anti-competitive agreements by ensuring that no cartel member deviates from their fixed price. For this, deviator is often punished by compelling it to compensate harmed firms. For the same purpose, information such as prices, sales data etc. are monitored on a regular basis, and data collection is a regular exercise in the whole process. Usually, cartel rely on self-reporting by a member for all the data that is being provided.
Herein, blockchain may help cartel to ensure that none of the members are deviating from cartel objectives. It may help cartel members to effectively share the data at a large scale and subsequently monitor the prices. The cartel will no longer have to rely on self-reporting by member firms and a transparent database in form of blockchain can be readily available for their evaluation.
It is pertinent to note that members of a cartel always have an incentive to deviate from the anti-competitive agreement in quest of capturing big profits. Therefore, cartels are usually difficult to sustain in long run. Herein, it is pertinent to note that better monitoring of cartel will give more credence to existence of a cartel. In case of blockchain, the information is updated in a real time basis and complete history of transaction is recorded. Since all the information will be publicly available, it will be easier for a cartel to detect any deviant behaviour of any cartelist.
Vertical Agreements
It has been observed in EU competition law jurisprudence that even a unilateral conduct, if accepted by other enterprise, can fall foul of concerted practice. That being the case, blockchain network may be used to prohibit enterprises to act independently of their own in a vertically integrated market. Since the information is available publicly, it would be easier to identify any deviation from the prescribed practice. Such transparency can force other players to tacitly accept the conditions imposed by vertically upward players. For example, it can be used to prohibit dealers/ retailers to provide discounts to consumers as the information regarding discount will be updated and visible to everyone on the chain. This may, in turn, lead to issues of resale price maintenance.
Hub and spoke cartel
In Hub and spokes arrangements are a horizontal restriction where a ‘hub’ facilitates coordination amongst two or more spokes, thereby facilitating a cartel without direct contact between two horizontal players.
In a private-permissionless blockchain: enterprises can engage in hub and spoke cartel by establishing a link between two blockchains. For example, a distributor can be a member of two rival supply networks based on blockchain. Such distributor can be a link for flow of information between two enterprises, thereby facilitating freely transfer of information. Therefore, two enterprises working through two distinct blockchains can also coordinate effectively to engage in anticompetitive activities.
Refusal to deal
Similarly, in a private blockchain created by one or more enterprises, it may be decided to not deal with any distributor or retailer. Private-Permissioned blockchains are distinguished from public blockchains in that the ability to write and commit transactions, and thus enjoy the facilities of the system, depend upon the permission granted to a user to access the blockchain. Such cases of refusal to deal are more critical in cases where access to any network is essential for the business. There may be a situation that certain players as well are prohibited from accessing the blockchain. This would be considered as a refusal to deal that may be violative of competition laws.
Tying
Furthermore, there can be an issue of tying supplementary products/ services that are outside the blockchain as a precondition to become a member of any blockchain. In this way, an enterprise or a group can engage in a traditional tie-in practices that may create adverse effect on competition, especially in a blockchain which is essential for any business. For example, there may be a situation that distributors of certain medicines are engaged in sale of drugs of certain pharmaceutical company, for which joining the blockchain of the company is essential. Herein, if the company decides to impose certain supplementary services unrelated to the core business, that may amount to tie-in and attract scrutiny under competition laws.
Predatory pricing
Usually in a blockchain, pricing is the transaction fee to add a block. For example, the amount is paid to the miners who verify the transaction in case of public blockchains such as Bitcoin. As the technology is developing, there may also be different pricing methods for a member to be added on certain blockchains. Since protocols can be changed easily in private blockchain, pricing can also be changed accordingly to the competition by other blockchain, which can also be used to engage in predatory pricing and consequently to foreclose the market. For example, we can take a market where several small businesses outsource their transaction to blockchain companies for certain fee. If there are multiple blockchains competing for users, any blockchain company may choose to take loss in transaction fee by burning out of their own pockets. Subsequently, once the competition is eliminated, transaction fees can be charged again at usual or perhaps higher amount. Therefore, issue of predatory pricing may be similar to what we encounter in traditional anti-competitive practices.
Regulatory Issues: Interventionist approach while protecting the core principles
One of the biggest concerns that come out are regarding regulation of blockchain. That because the blockchain is decentralised, immutable and anonymous, it might be difficult for competition authorities to regulate/ enforce competition law in blockchain regime. Even though it would depend on the protocols on which a blockchain works, in many cases, for competition authorities to effectively regulate the blockchain, there must be an intervention mechanism.
Once we decide that there must be an intervention mechanism, the follow up question is that how can such an intervention mechanism be implemented? It has been argued by Dr. Thibault Schrepel that for such implementation ‘law has to become code’. This means that basic rules of governance must be implemented in the protocols of blockchain right from starting. However, for doing so, competition authorities must build trust that such an intervention measures would not be misused as that would kill the incentive to use the technology itself. It can be framed in a manner that identity of an individual would be only revealed in case of reasonable grounds that there has been any violation.
The point to be taken into consideration while making such policy decisions is that the approach must be a balanced so that it does not disrupt a new technology which is considered as revolutionary as internet. This can be achieved only by ensuring that core principles on which blockchain rests are not interfered with.